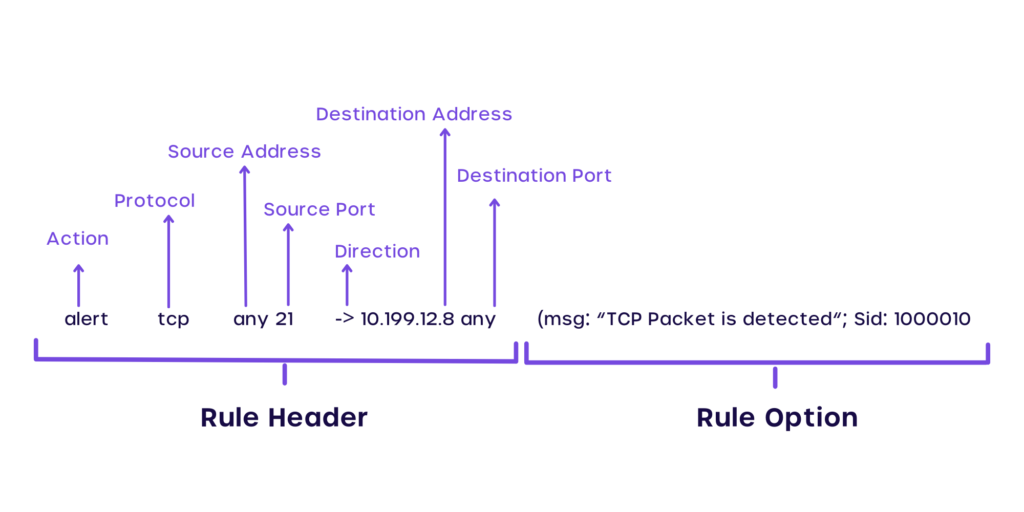
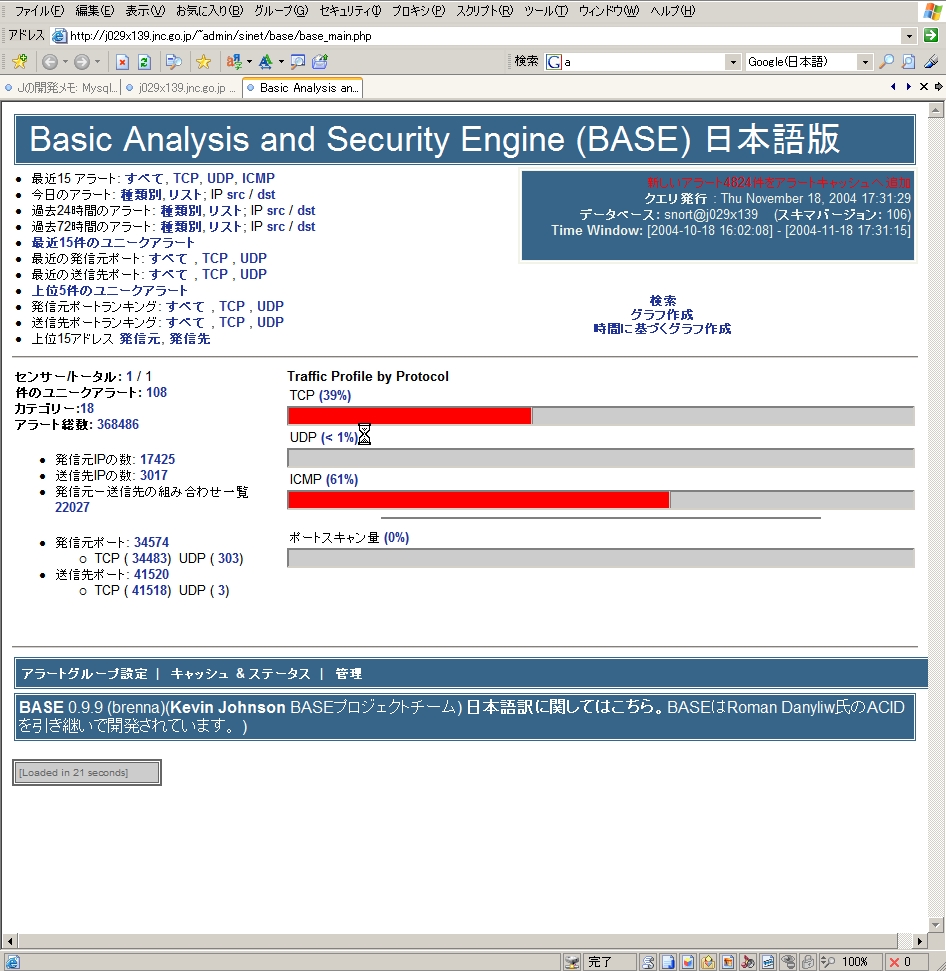
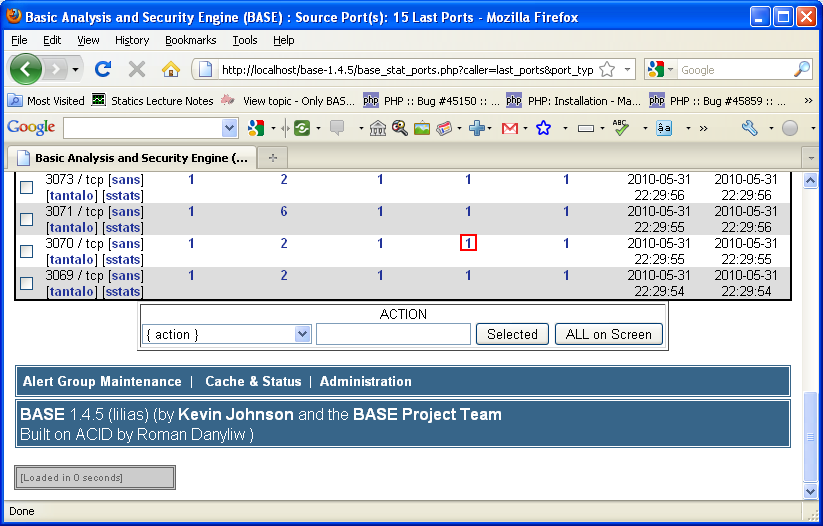
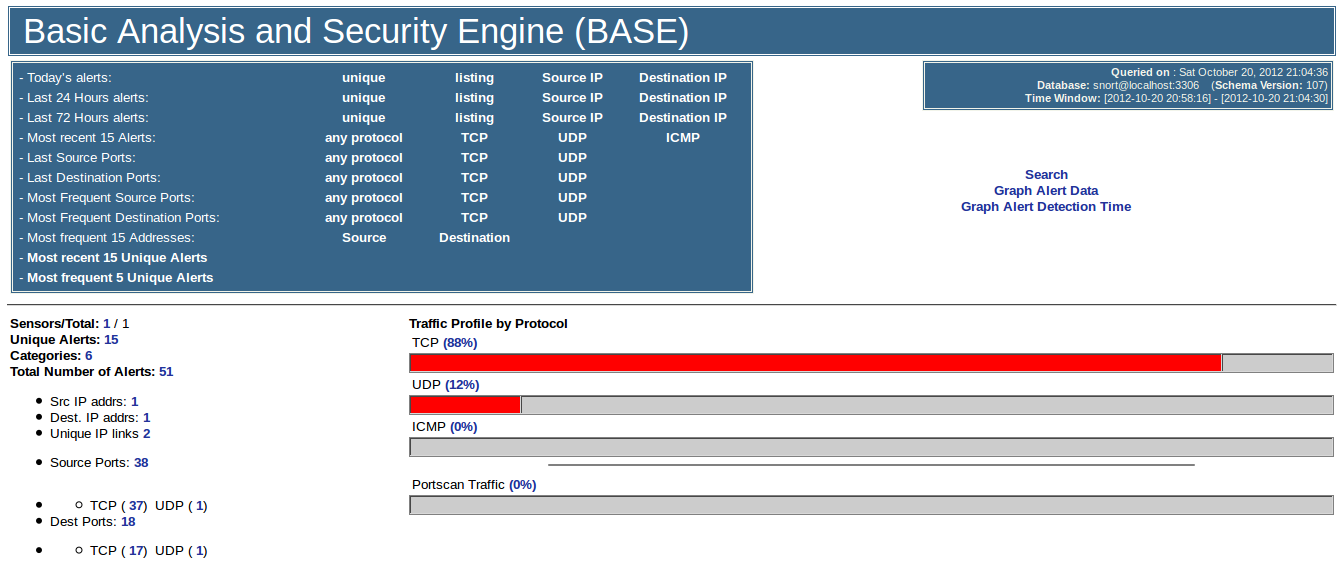
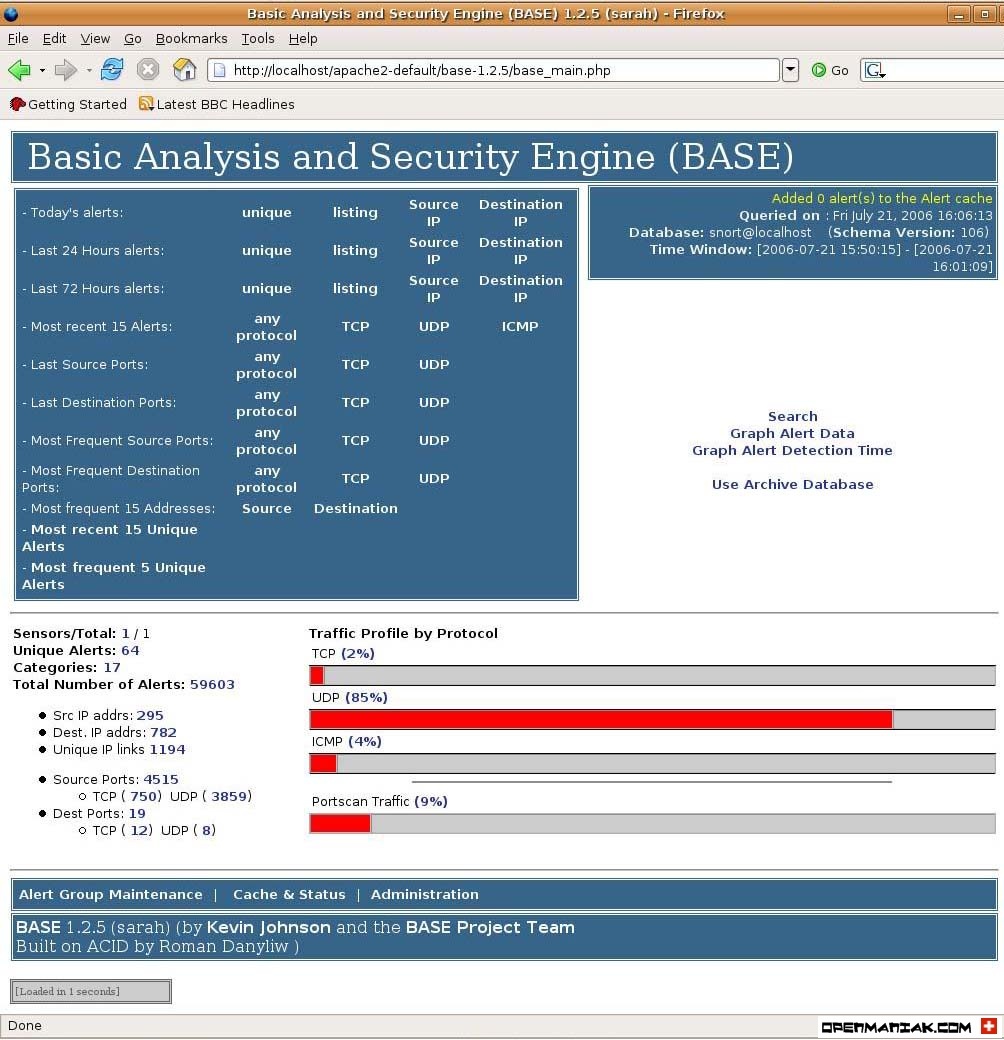
Hack Like a Pro: Snort IDS for the Aspiring Hacker, Part 2 (Setting Up the Basic Configuration) « Null Byte :: WonderHowTo

Figure 8 from Rule-Based Network Intrusion Detection System for Port Scanning with Efficient Port Scan Detection Rules Using Snort | Semantic Scholar
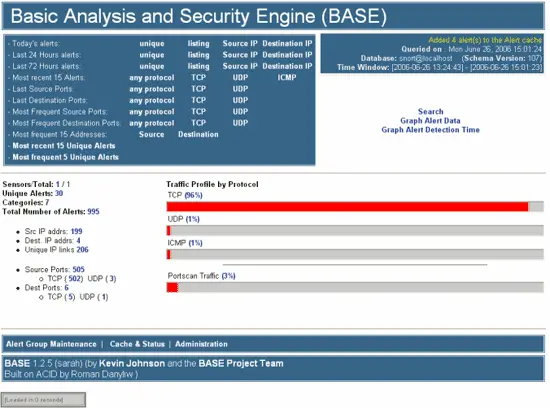
Intrusion Detection System using SNORT & BASE (Basic Analysis and Security Engine) Prepared By: Tahira Farid & Anitha Prahladachar Course: Winter. - ppt download
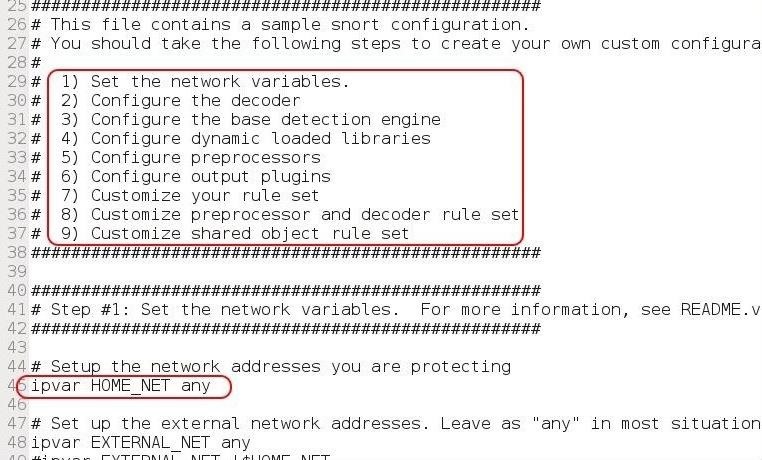
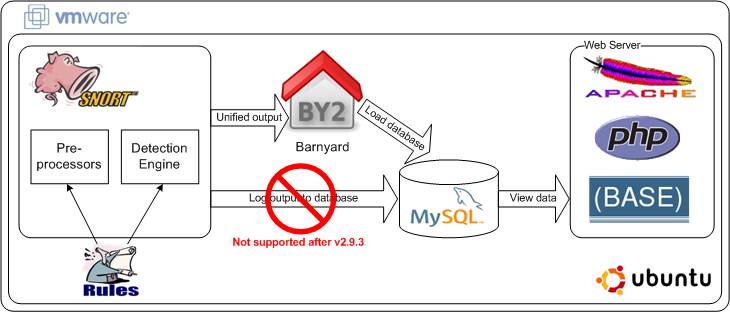
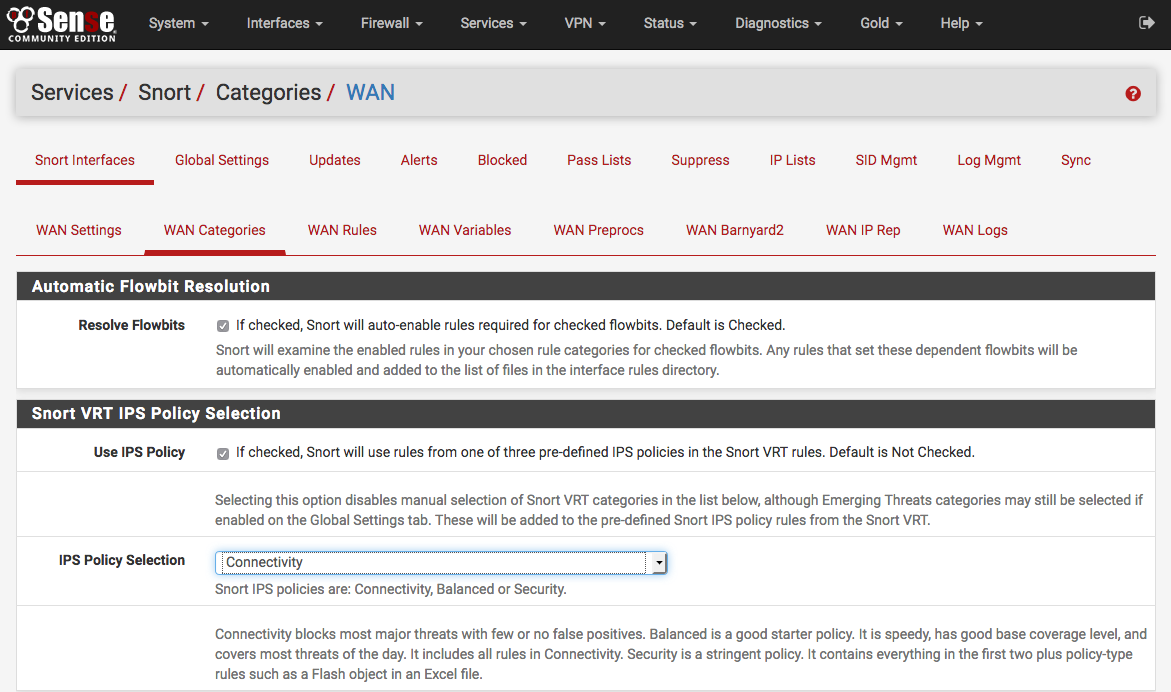
![IDS]How to configure Snort. Objectives | by Takahiro Oda | Medium IDS]How to configure Snort. Objectives | by Takahiro Oda | Medium](https://miro.medium.com/v2/resize:fit:1400/0*yhOMs9eb1Q70nsPl.png)